Cyber Security - Flash Networks
The Harmony Security module blocks access to any malicious destination. It protects the attack at the connection initiation.
Subscribers rely on mobile operators to protect them from cyber-attacks. Use this opportunity.
Harmony Security from Flash Networks differs from other security solutions on the market. There is no need for installation on the device. Plus, the subscriber receives an SMS for the prevented threat. A history and control policy is available for the subscriber to follow.
Pitch your own, branded security solution to the mass market while you generate revenue.

Flash Solution Integration Seamlessly
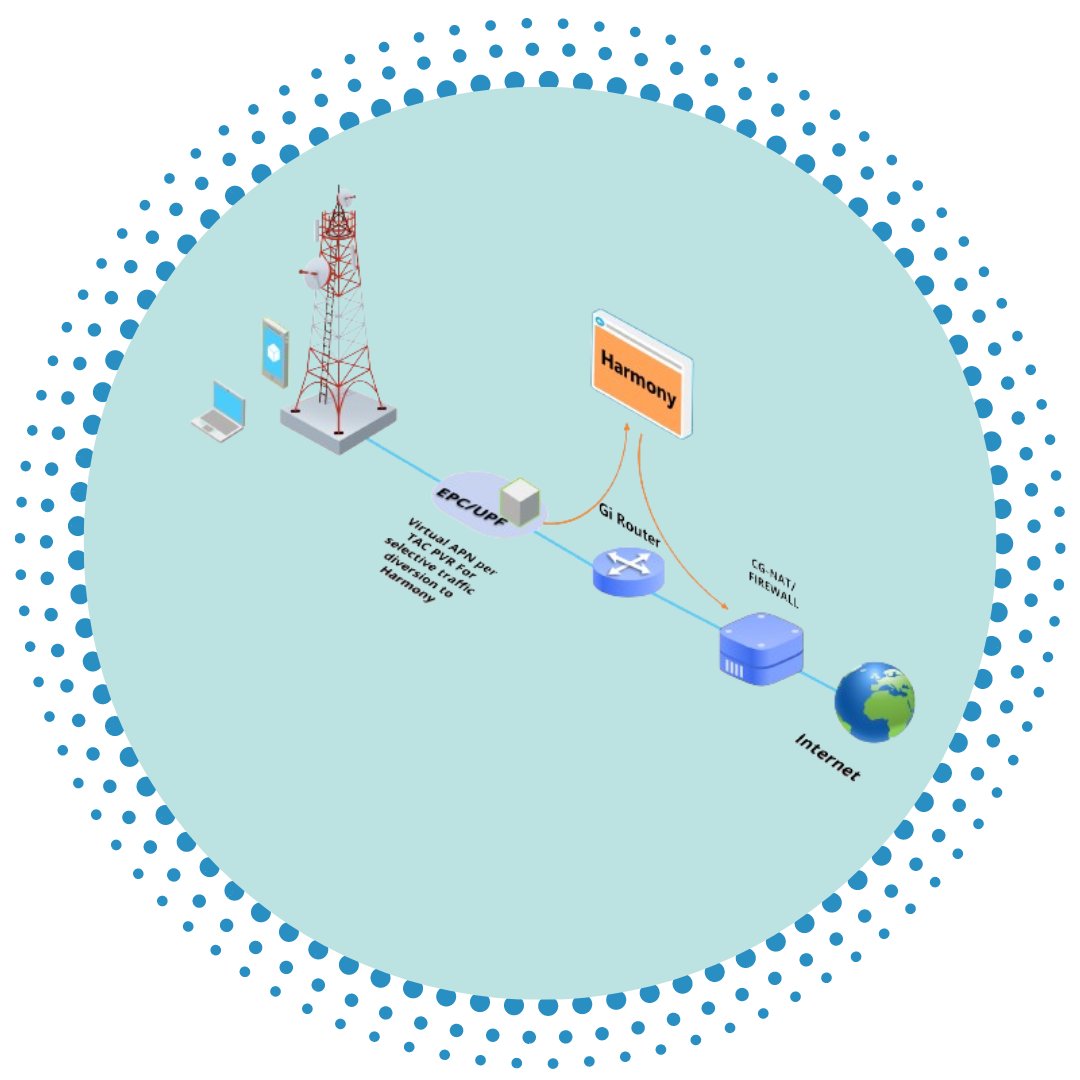
A central transparent platform that flows data securely to/from user equipmentIntegrated with top Core vendors: Ericsson, Nokia, ZTE, Huawei
It supports mobile (3G, 4G, 5G), enterprise, and home internet
Fully SDN/NFV deployed supporting VM and cloud-native containers
Policy Based and Flexible platform that enables better control of multiple service
Benefits for the operator
Immediate Protection
Flash Networks Harmony Security module protects any new connection at the connection initiation.
No Installation needed
The security protection works seamlessly on any SIM card device, with no limitations on OS or CPU. Compatible with all types of networks and transport technologies
History and control Panel
Operators can send subscribers branded SMS notification that informs the user for the prevented threat.
Brand Differentiation
Harmony Security Module allows operators to enhance their portfolio and gain trust among subscribers.
Benefits for the user
Prevent Unauthorized Access
Flash Networks Harmony Security module protects any new connection at the connection initiation.
Nothing to Install on the Device
Peace of mind
With implemented Harmony Security end users can enjoy safe browsing. Enterprises can be calm that hacker and terrorist attacks can`t do damage to company network and devices.
The Latest Attacks and Breaches
Monti ransomware gang has claimed responsibility for a cyber-attack on New Zealand’s third-largest university, Auckland University of Technology. The threat actors claim to have stolen 60 GB of data, giving the victim a deadline of October 9th to pay a ransom.
Insider threat incidents have risen 44% over the past two years, with costs per incident up more than a third to $15.38 million.
By 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.
Source: Checkpoint
Resources
Videos
Use Case
Security threat notification
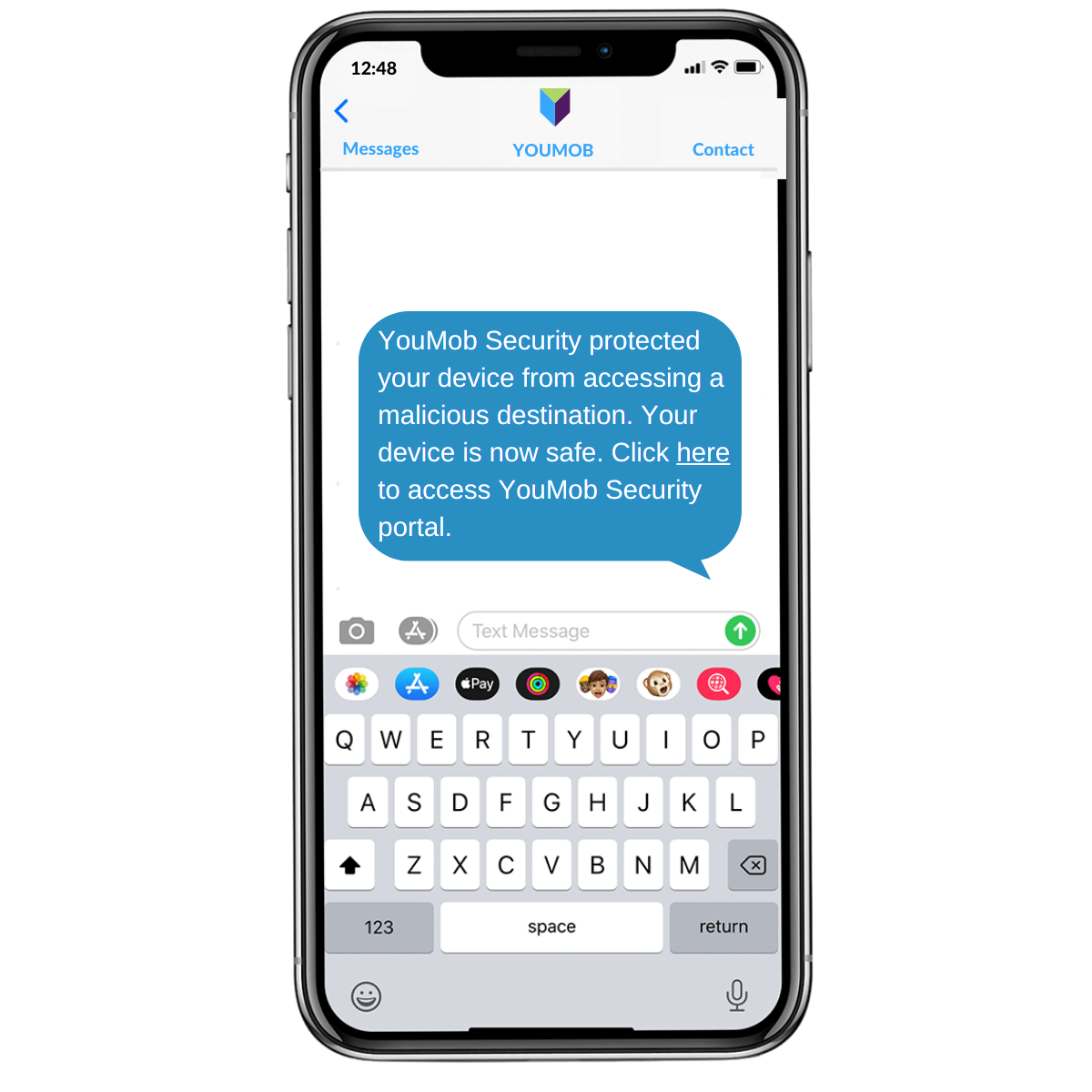
Subscribers receive a notification with the operator's logo informing them that access to harmful destinations is blocked by the security platform.






