IoT Security from Flash Networks
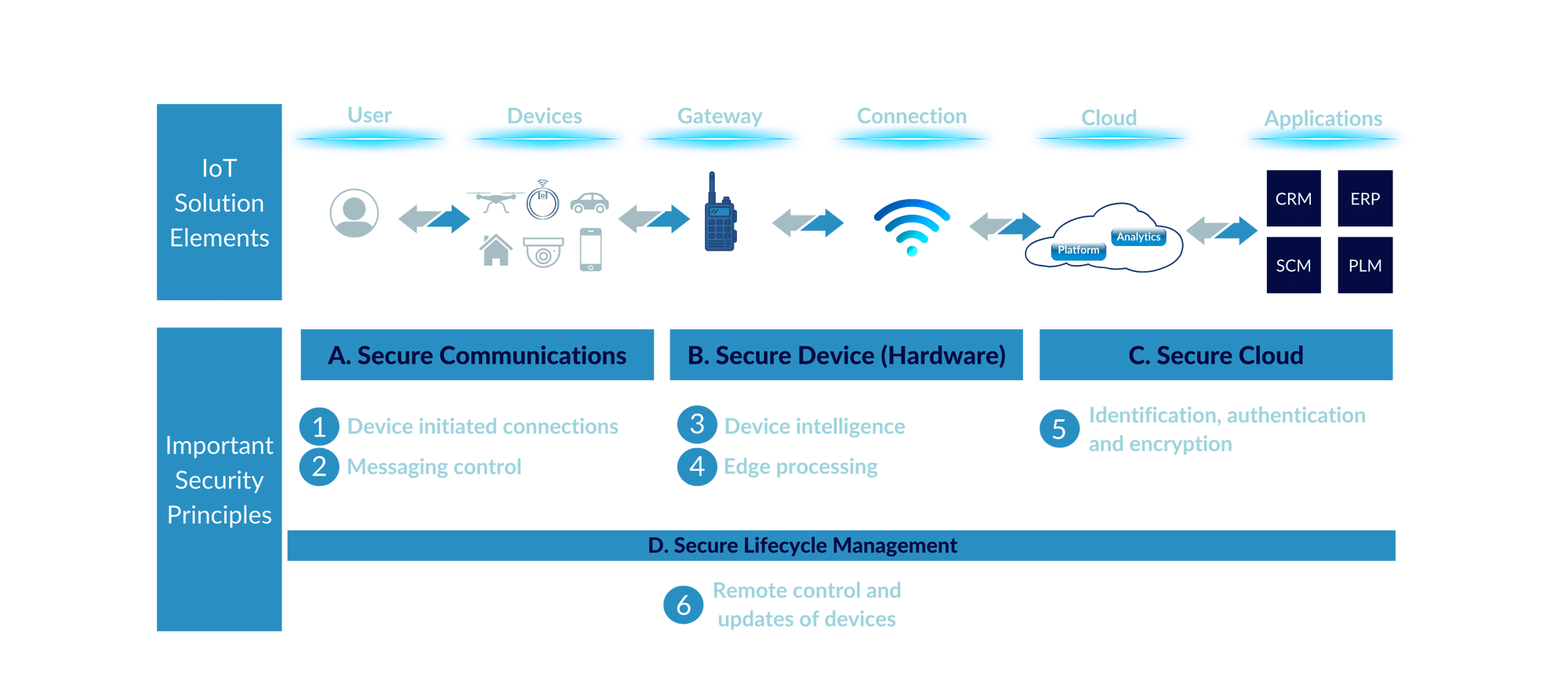
Six Principles of IoT
Benefits for the operator
Fast Protection
No Installation needed
The security protection works seamlessly on any SIM card device, with no limitations on OS or CPU. Compatible with all types of networks and transport technologies
History and control Panel
Operators can send subscribers branded SMS notification that informs the user for the prevented threat.
Brand Differentiation
Harmony Security Module allows operators to enhance their portfolio and gain trust among subscribers.
Benefits for the User
Prevent Unauthorized Access
Flash Networks Harmony Security module protects any new connection at the connection initiation. Subscribers receive SMS notification for the prevented threat.
No Installation Needed
There is no need for the user to install an app. Security protection works seamlessly on any SIM card device, with no limitations on OS or CPU. Compatible with all types of networks and transport technologies.
Piece of Mind
By implementing security, companies can demonstrate their commitment to protecting sensitive information and ensuring a safe online environment. This is important for the brand image.
Top 4 IoT Security threats and risks

Botnets
A botnet in the IoT refers to a collective of compromised or infected IoT devices that are under the control of cybercriminals and used for harmful activities such as launching DDoS attacks or stealing sensitive data.

DNS Threats
The value of IoT technology lies in its ability to connect devices, gather data, and make decisions based on analysis. However, the current naming system used for device connections, known as DNS, is outdated and unreliable for the scale, traffic, and security demands of today's IoT.

IoT Ransomware
The purpose of using IoT ransomware is to strike the target at a specific time and place when they are unable to reset the device or counter the effects of the ransomware. The goal is to create a sense of urgency and encourage the target to pay the ransom.

Shadow IoT
The use of IoT devices by employees within an organization, without IT's knowledge, is commonly referred to as Shadow IoT. Such devices include personal tablets, mobile devices, smart speakers, and others.
Resources
Videos
Use Case
Security threat notification
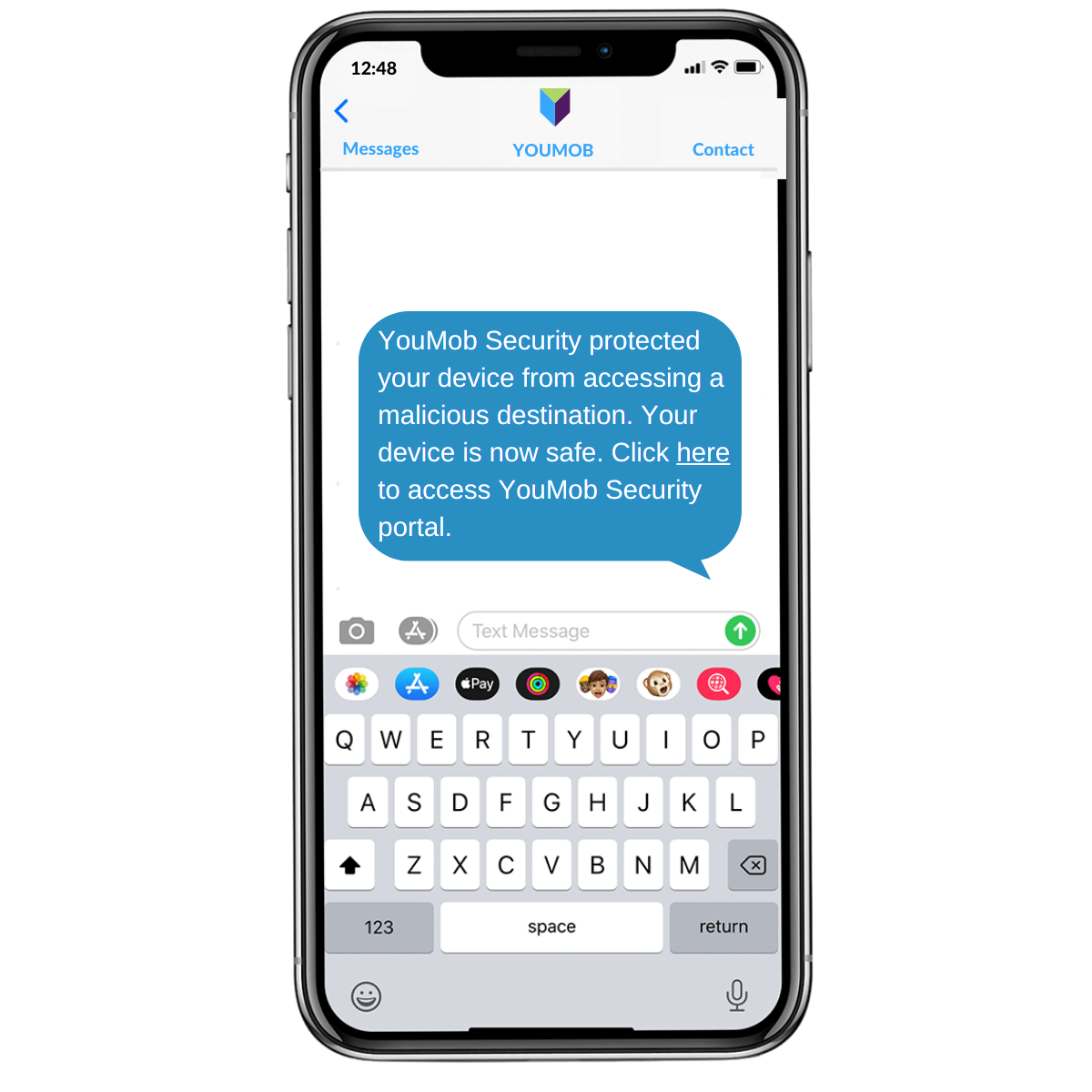
Subscribers receive a notification with the operator's logo informing them that access to harmful destinations is blocked by the security platform.
